The following best practices can be performed internally andor using external resources. The corrective actions obtained by OCR from covered entities have resulted in systemic change that has improved the privacy protection of health information for all individuals they serve.

Dominican Republic 2021 Article Iv Consultation Press Release Staff Report And Statement By The Executive Director For Dominican Republic In Imf Staff Country Reports Volume 2021 Issue 169 2021
View results Is it true that A breach as defined by the DoD is.

. Since 2003 OCRs enforcement activities have obtained significant results that have improved the privacy practices of covered entities. Regularly monitor networks and databases for unusual traffic. Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when it is unattended Promptly retrieve documents containing PHIPHI from the printer All of this above correct 1 Under HIPAA a covered entity CE is defined as.
All of the above You can help prevent a breach by accessing only the minimum amount of PHIPII necessary and by promptly retrieving documents containing PHIPII from the printer. Perform suspicious email training exercises to help employees identify potentially nefarious emails. Additionally DLP tools and software are used to.
Its safe to say that cyber security is a top concern for CEOs todaya recent survey by PWC found that 87 percent of CEOs feel somewhat-to-extreme concern about cyber security. And it should be. Which of the following are breach prevention best practices.
Before you can prevent a data breach you need to know the sensitive data you collect store transmit or process. Which of the following are breach prevention best practices. Cybercriminals target non-public personal information NPI.
You might also consider the following recommendations. Invest in security automation. All of the above You can help prevent a breach by accessing only the minimum amount of PHIPII necessary and by promptly retrieving documents containing PHIPII from the printer.
Develop and test an incident response plan IRP. Create a strong password policy and enforce it. Identity sensitive data collected stored transmitted or processes.
Safeguard PHI with Encryption to Prevent a HIPAA Data Breach. If a breach affects fewer than 500 individuals the covered entity must notify affected individuals without reasonable delay and no later than 60 days after discovery of the breach and HHS no later than 60 days after the end of the calendar year in which the breach occurred. CEOs are being held increasingly accountable for their companys data breach failures and in extreme cases like Target and Sony have lost.
You should always logoff or lock your workstation when it is unattended for any length of time. Data loss prevention systems can help detect data breach instances and prevent data leak or transfer trough monitoring and blocking sensitive data while in transit in use and at rest. The following are high-level best practices for preventing breaches.
Which of the following are breach prevention best practices. Invest in up-to-date data loss prevention DLP technology. 20 Which of the following are breach prevention best practices.
Which of the following are categories for punishing violations of federal health care laws. Confidentiality Integrity and Availability are the fundamental objectives of health information security and the HIPAA Security Rule requires covered entities and business associates to protect against threats and hazards to these. Click to see full answer Regarding this which of the following are fundamental objectives of information security quizlet.
You should always logoff or lock your workstation when it is unattended for any length of time. Breach Notification Rule - 45 CFR 164400-414 If an impermissible use of disclosure of PHI is determined to be a Breach CEs must provide notification of the Breach to affected individuals the Secretary of HHS The Secretary state entities under applicable state law and in certain circumstances to the media Reputation. - Keep track of a myriad of federal and state level laws and regulations concerning.
For a more in-depth discussion about your organizations breach prevention strategy contact Securance for a. What are breach prevention best practices. Properly configure the cloud.
All of this above answer Access only the minimum amount of PHIpersonally identifiable information PII necessary. Train employees on data security practices and awareness. However these 30 best practices for preventing a data breach can reduce the risk and respond to an attack more effectively.
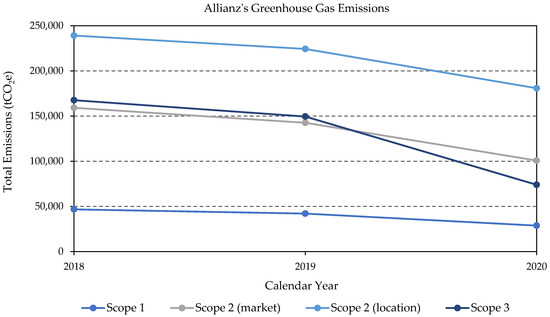
Sustainability February 2 2022 Browse Articles

Amulet Winery Investors Sue Tuck And Boo Beckstoffer Alleging Breach Napa Valley Wineries Meadowood Napa Valley Winery

The Parent Toolkit App Text Toolkit To 33733 To Get The App On Your Mobile Device Now The Parent Toolkit App Is Designed To Help You N Technology Pinte

4 Practical Techniques And Countermeasures To Battle Ransomware Carbon Black Prevention Cyber Security Optimization

Fintech Inclusive Growth And Cyber Risks Focus On The Menap And Cca Regions In Imf Working Papers Volume 2018 Issue 201 2018
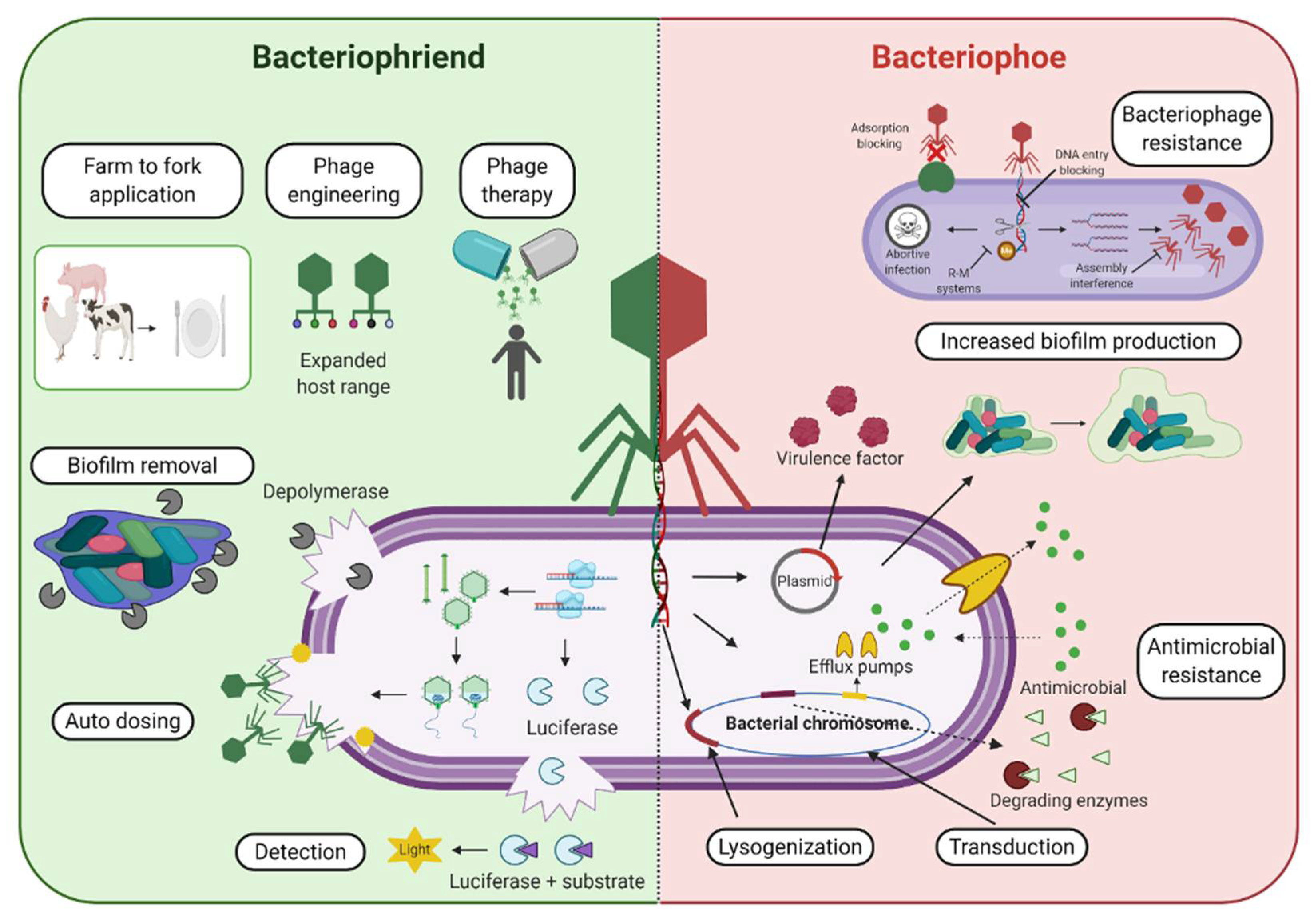
Pharmaceuticals Free Full Text The Age Of Phage Friend Or Foe In The New Dawn Of Therapeutic And Biocontrol Applications Html

How Not To Greet A Dog 11 X 14 Kid Friendly Poster Zazzle Com In 2022 Dog Biting Dog Body Language Dog Language

12 Ways To Protect Your Business From A Ransomware Attack Infographic Cybersecurity Infographic Infographic Cyber Security

The Five Most Common Attack Patterns Behind Today S Data Breaches Tripwire Cyber Security Tech Apps

Pdf All One Needs To Know About Metaverse A Complete Survey On Technological Singularity Virtual Ecosystem And Research Agenda

What Is The Need Of Ip Addresses Restriction In Enterprises Understand The Importance Of Implementing Ip Add In 2021 Cloud Data Internet Protocol Address Ip Address

The Job Of Dataprotection Is Getting Tougher Every Day And Minor Mistakes Can Cost Any Organization Thousands Of Dollars Data Loss Prevention Data Loss Data

Businessman Login With Fingerprint Scanning Technology Fingerprint Digital Lock Fingerprint Lock

Jeannieborin On Twitter Yahoo News How To Plan Finance
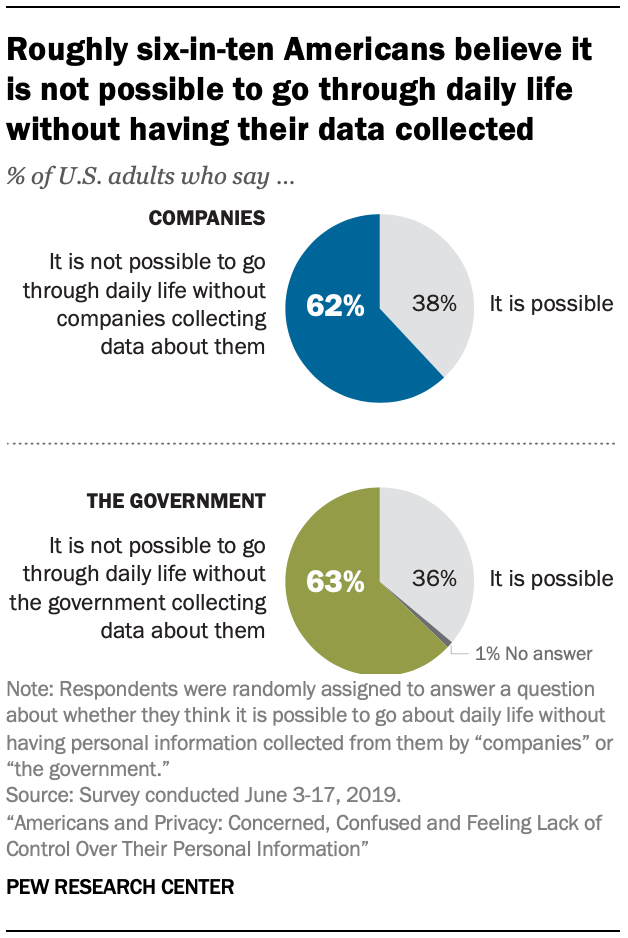
Americans And Privacy Concerned Confused And Feeling Lack Of Control Over Their Personal Information Pew Research Center
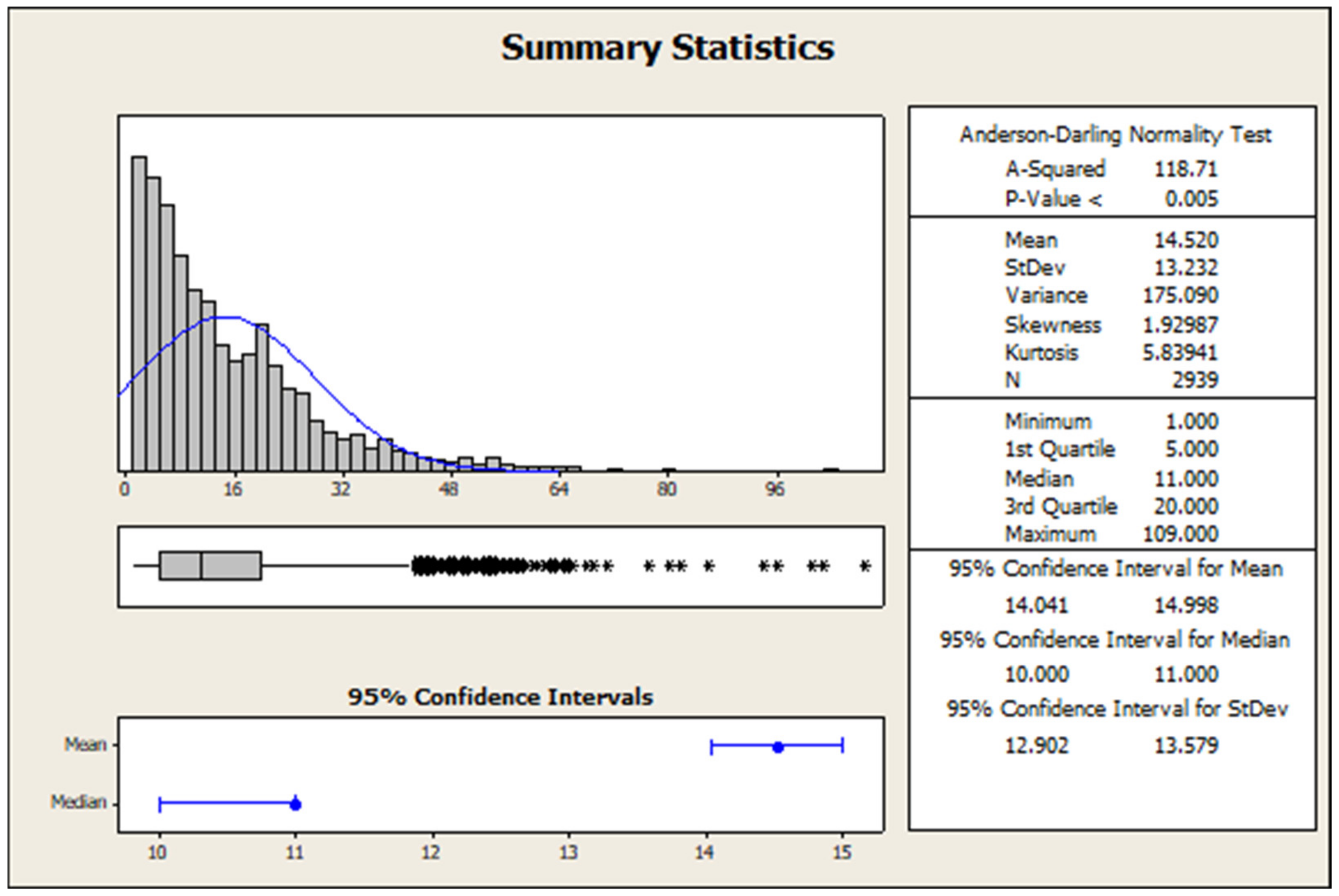
Sustainability Free Full Text Sustainability Of Railway Undertaking Services With Lean Philosophy In Risk Management Case Study Html

Fintech Inclusive Growth And Cyber Risks Focus On The Menap And Cca Regions In Imf Working Papers Volume 2018 Issue 201 2018

Guidesforbackup On Twitter Software Security Wordpress Security Cyber Security
